
June 25, 2025
June 26, 2025
-
min read

June 25, 2025
June 26, 2025
-
min read

June 26, 2025
June 25, 2025
-
min read

June 26, 2025
June 25, 2025
-
min read
.svg)
February 10, 2026
February 10, 2026
-
3
min read
.svg)
February 10, 2026
February 10, 2026
-
3
min read
.svg)
.svg)
February 10, 2026
February 10, 2026
-
3
min read
.svg)
February 10, 2026
February 10, 2026
-
3
min read

December 15, 2025
December 16, 2025
-
3
min read

December 16, 2025
December 15, 2025
-
3
min read


December 15, 2025
December 16, 2025
-
3
min read

December 16, 2025
December 15, 2025
-
3
min read
.svg)
December 10, 2025
December 16, 2025
-
3
min read
.svg)
December 16, 2025
December 10, 2025
-
3
min read
.svg)
.svg)
December 10, 2025
December 16, 2025
-
3
min read
.svg)
December 16, 2025
December 10, 2025
-
3
min read
.jpeg)
July 31, 2025
July 31, 2025
-
3
min read
.jpeg)
July 31, 2025
July 31, 2025
-
3
min read
.jpeg)
.jpeg)
July 31, 2025
July 31, 2025
-
3
min read
.jpeg)
July 31, 2025
July 31, 2025
-
3
min read
.png)
April 24, 2025
May 19, 2025
-
3
min read
.png)
May 19, 2025
April 24, 2025
-
3
min read
.png)
.png)
April 24, 2025
May 19, 2025
-
3
min read
.png)
May 19, 2025
April 24, 2025
-
3
min read
.png)
April 25, 2025
May 19, 2025
-
3
min read
.png)
May 19, 2025
April 25, 2025
-
3
min read
.png)
.png)
April 25, 2025
May 19, 2025
-
3
min read
.png)
May 19, 2025
April 25, 2025
-
3
min read
.png)
April 25, 2025
May 19, 2025
-
4
min read
.png)
May 19, 2025
April 25, 2025
-
4
min read
.png)
.png)
April 25, 2025
May 19, 2025
-
4
min read
.png)
May 19, 2025
April 25, 2025
-
4
min read
April 24, 2025
April 24, 2025
-
3
min read
April 24, 2025
April 24, 2025
-
3
min read
April 24, 2025
April 24, 2025
-
3
min read
April 24, 2025
April 24, 2025
-
3
min read

June 6, 2024
December 16, 2025
-
min read

December 16, 2025
June 6, 2024
-
min read


June 6, 2024
December 16, 2025
-
min read

December 16, 2025
June 6, 2024
-
min read
February 23, 2026
February 23, 2026
-
min read
February 23, 2026
February 23, 2026
-
min read
February 23, 2026
February 23, 2026
-
min read
February 23, 2026
February 23, 2026
-
min read
July 30, 2025
July 30, 2025
-
min read
July 30, 2025
July 30, 2025
-
min read
July 30, 2025
July 30, 2025
-
min read
July 30, 2025
July 30, 2025
-
min read

June 10, 2025
June 10, 2025
-
min read

June 10, 2025
June 10, 2025
-
min read

June 10, 2025
June 10, 2025
-
min read

June 10, 2025
June 10, 2025
-
min read
May 28, 2025
June 12, 2025
-
min read
May 28, 2025
June 12, 2025
-
min read
May 28, 2025
June 12, 2025
-
min read
May 28, 2025
June 12, 2025
-
min read

February 1, 2026
-
4
min read

February 1, 2026
-
4
min read

December 3, 2025
-
min read

December 3, 2025
-
min read

September 30, 2025
-
5
min read

September 30, 2025
-
5
min read

September 18, 2025
-
5
min read

September 18, 2025
-
5
min read

September 9, 2025
-
4
min read

September 9, 2025
-
4
min read

September 5, 2025
-
min read

September 5, 2025
-
min read

August 14, 2025
-
5
min read

August 14, 2025
-
5
min read
.png)
July 21, 2025
-
5
min read
.png)
July 21, 2025
-
5
min read
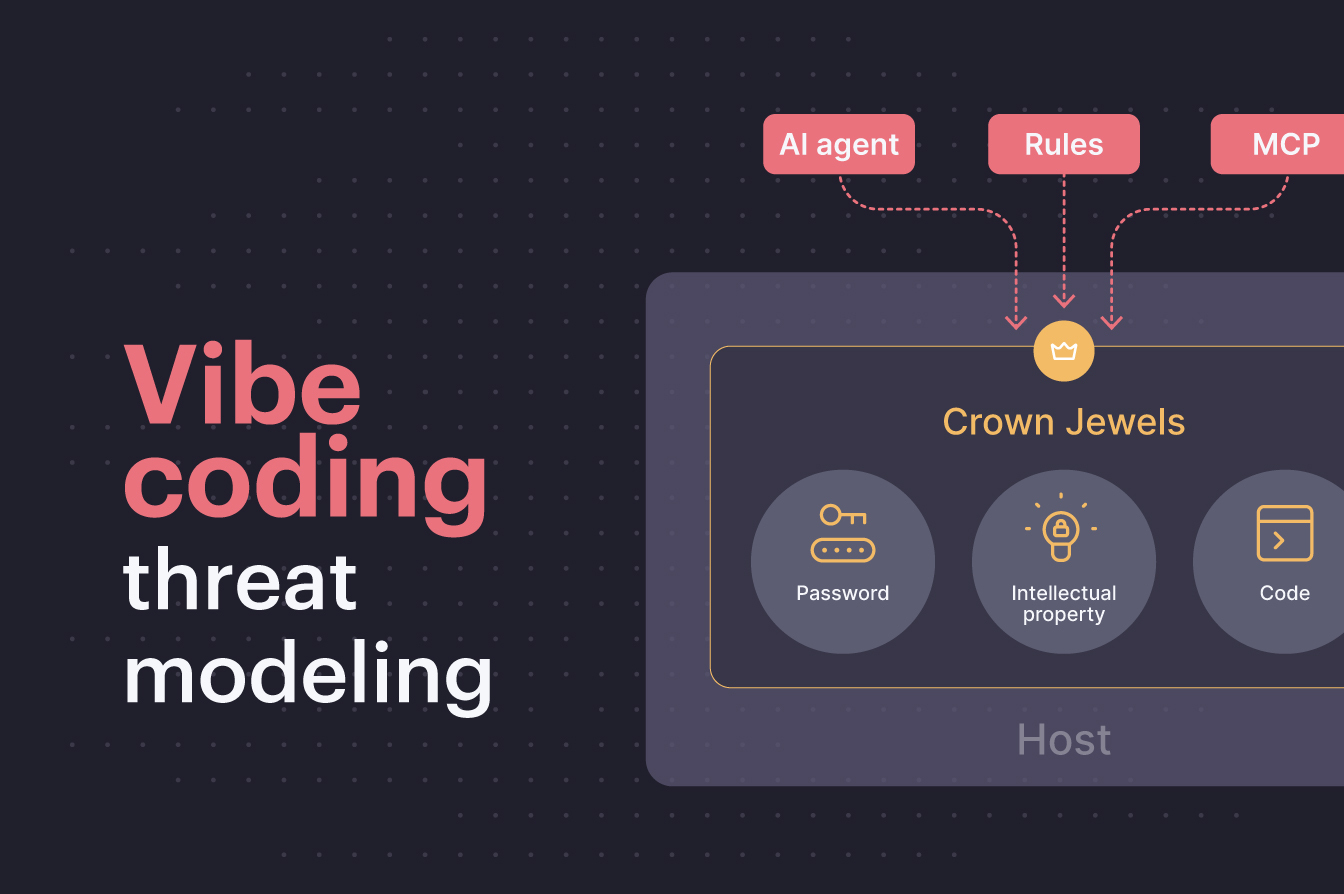
July 7, 2025
-
3
min read

July 7, 2025
-
3
min read

June 25, 2025
-
5
min read

June 25, 2025
-
5
min read